The electronic signature
The first signature solution in Tunisia

Sign your documents for free in minutes
Our eSignature app provides you with an easy way to legally sign all your documents anytime from any device for free.
By making it easy to sign documents electronically, our solution eliminates the need for slow and costly paper-based signing processes, while inking legal signatures that provide integrity, trust and regulatory compliance.

Signing is legal
Getting your documents signed online not only saves time and money, it's also legal.
- Our solution is approved by the National Electronic Certification Agency and meets a proven legal framework.
- Our signatures implement all ETSI signature standards, including XAdES, PAdES, CAdES, qualified signatures that respect the law on exchanges and e-commerce in Tunisia.
Legal framework of the electronic signature in Tunisia
Tunisia has promulgated a law on electronic commerce: the law n ° 2000-83 of August 9th, 2000, relative to the exchanges and the electronic commerce, defined the electronic certificate and the electronic signature, favoring an environment favorable to the development of the exchanges and e-commerce, and allowed the creation of the National Electronic Certification Agency (ANCE) root authority of electronic certification in Tunisia, in order to represent the highest level of trust in the field of electronic certification, security of transactions and electronic exchanges.
The National Agency for Electronic Certification (ANCE) has the main vocation of securing electronic exchanges in various fields such as e-commerce, e-government, e-Banking, e-finance, e-commerce and e-commerce. as well as e-health ... Its role is to secure payment transactions and the authentication of different players.
Thus any person wishing to perform a payment transaction on a secure site with a certificate from the National Agency of Electronic Certification can be sure that it addresses a reliable site and that all the data that it communicates are secure. The other main missions of ANCE are:
- Establish mutual recognition agreements with foreign Certification Authorities.
- Manage electronic certificates (generation, revocation, publication and retention of certificates).
- Grant electronic certification service provider activity authorizations.
- Define the technical characteristics of signature and signature verification devices.
- Perform the certification of encryption systems.
The ANCE essentially delivers two types of electronic certificates:
- Certificate of signature: which allows to associate the identity of a person to a public key. It can be used to sign, encrypt e-mail and authenticate during a secure session, such as when consulting your bank account, tax return, CNSS, CNRPS, CCP net, and customs declaration, etc. ....
- Server certificate: It associates the identity of a web server with a public key. It allows secure exchanges between the server and its customers during the establishment of a secure session for example for the purchase or payment online on a merchant site.
FAQ on the electronic signature

What is an electronic signature?
A handwritten signature consists of affixing a personal mark on a
paper document. It expresses the will of the signatory and his
agreement with the content of the document. Transposed in the
electronic world, the electronic signature has the same legal
value as the handwritten signature. .
The electronic
signature consists of three components:
- The document carrying the signature.
- The signature itself.
- The electronic certificate authenticating the signatory.
Is the electronic signature visible on the signed document ?
The electronic signature differs from the written signature in that it is not visual but corresponds to a number or a series of numbers.
Indeed, the action of digitally signing produces binary
information commonly called electronic signature. A document may
contain several electronic signatures.
What types of files can be signed electronically ?
All types of files without exception can be signed (Word documents, PDF, XML, etc.). The most used file format is the PDF, for its portability and also the possibility of affixing several electronic signatures. But also standardized XML files for exchanges between public entities.
What is the use of the electronic signature ?
Like handwritten signatures, electronic signatures are used to
identify co-signatories (authors) of electronic data (an email
for example).
Electronic signatures can guarantee the
following security properties:
- >Authentication: Verifying the identity of a person (or a host: server and client). This guarantees the identity of the person who signed the data: the origin of the message, the document or the transaction is indisputable.
- Confidentiality and Data Integrity: The electronic signature protects the integrity of the data. This means that the document received has not been tampered with, voluntarily or involuntarily. Otherwise, the document is flagged as having been modified.
- Non-repudiation: the signatory of a document proves his identity. Non-repudiation establishes, later, who participated in a transaction. The sender can not deny having sent the message and the addressee can not deny having received it. Simply, non-repudiation means that information can not be rejected, just as with handwritten signatures.
Electronic signatures are created and verified through electronic certificates.
What is an electronic certificate ?
An electronic certificate is a document in electronic form that aims to authenticate the identity of the signatory: it is the identity card of the electronic world.
What does an electronic certificate contain ?
The information contained in the electronic certificate is as
follows:
- The name of the certificate holder.
- The validity start date of the certificate.
- The organization to which the wearer belongs (if necessary).
- The address to find the Certificate Revocation Lists (CRLs).
- The name of the trusted company, that is, the authority that issued the electronic certificate.
- The signature of this authority on this certificate.
- Possibly the photograph of the wearer or the logo of the company.
- etc…
The electronic certificate is divided into two parts :
- The first part contains the information.
- The second part contains the signature of the authority that issued the certificate.
Who issues the electronic certificate ?
The electronic certificate must be issued by a Certification
Authority (CA) which is an organization recognized as competent
to issue certificates to a population with which it has full
confidence and to ensure their validity. It commits itself to the
identity of a person through the electronic certificate that it
gives him.
A certifying authority is responsible
(vis-à-vis its customers, but also anyone relying on an
electronic certificate it has issued) for the entire
certification process and, consequently, for the validity of the
certificates it issues. In addition, it defines the certification
policy and enforces it.
A certification authority is
organized around three basic functions:
- Organization function: processing certificate requests, checking information, validating or rejecting requests, revoking certificates.
- Technical function: responsible for the production of electronic certificates, secure end-to-end environment.
- Certificate Distribution Function
How to sign a document ?
When you sign a document, the signature software creates a digital fingerprint called a hash: a kind of digital digest consisting of a series of letters and numbers. The hash is unique (the smallest change in the document will produce a different hash). This hash is then encrypted (encrypted) using the private key of your digital certificate. The encrypted hash and the public key are together to compose the digital signature, appended to the document.
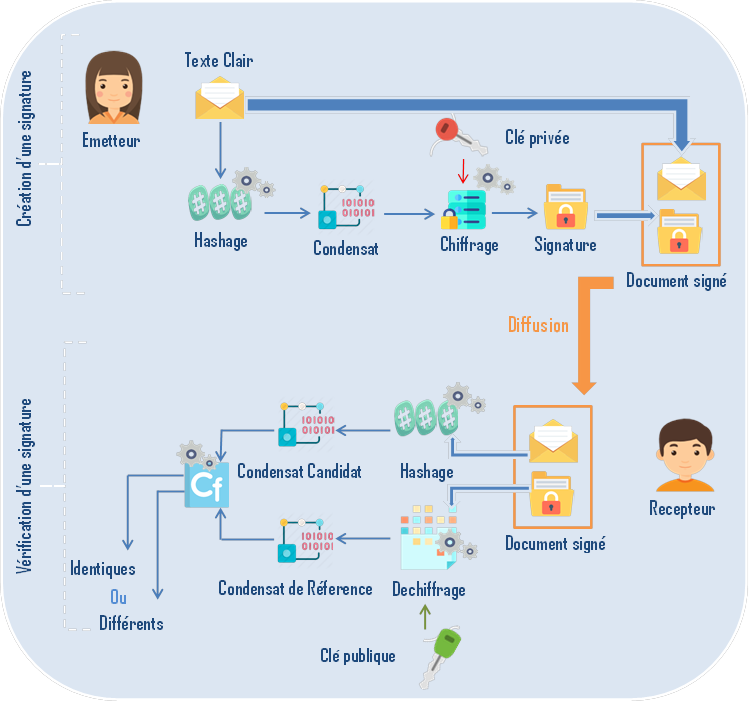
How to check a signature ?
When the signed document is opened, the hash is decrypted using
the signer's public key. Then the verification software
recalculates the hash of the document: if it is identical to the
hash previously decrypted, the document has not been modified.
The software then displays a message certifying its integrity, as
well as the signatory's name.
So the principle of the
electronic signature rests on two families of algorithms, which
will be used in a complementary way:
It is strongly recommended to associate a timestamp with each electronic signature.
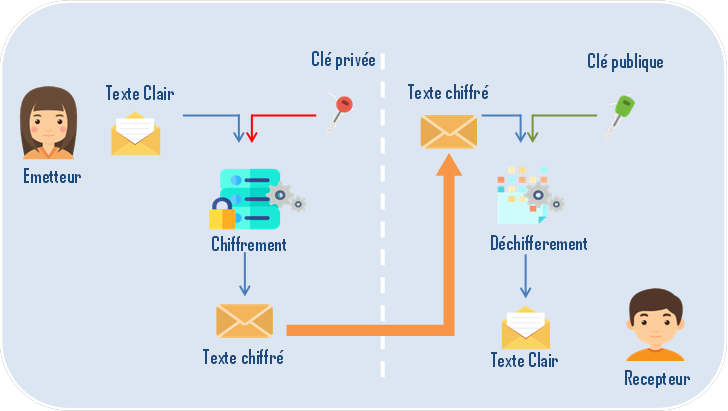
What is a symmetric encryption algorithm ?
The principle of an asymmetric algorithm is simple.
A pair of digital keys is constructed in such a way that the cryptogram (encrypted text) generated from a clear text and one of the keys can be easily found only with the other key.
In practice, one of the keys is secretly kept: private key, while the other is public: public key.
Only the owner of a private key (the emitter in our example) could have encrypted a decrypted text with the associated public key.
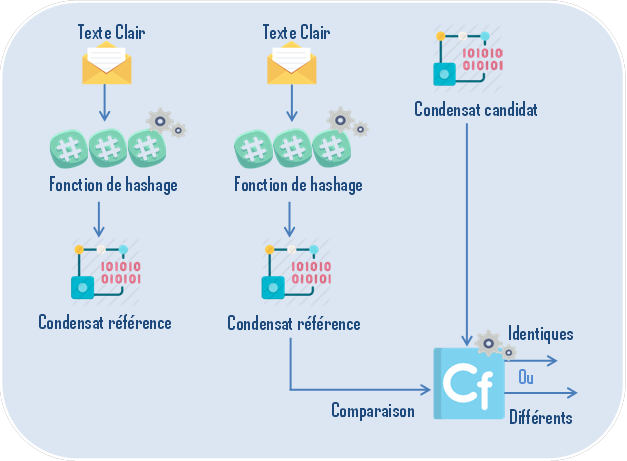
What is a hash function?
Is a one-way, collision-free function that calculates a fixed-size (or condensate) footprint from data of varying sizes. These functions are one-way because you can not find the original data from the fingerprint.
A function is said to be collision-free or injective when it is
deemed very difficult to find two different sources leading to
the same result.
The calculation of the condensate of a
document and the comparison of it with its initial value makes it
possible to control the integrity of a document.
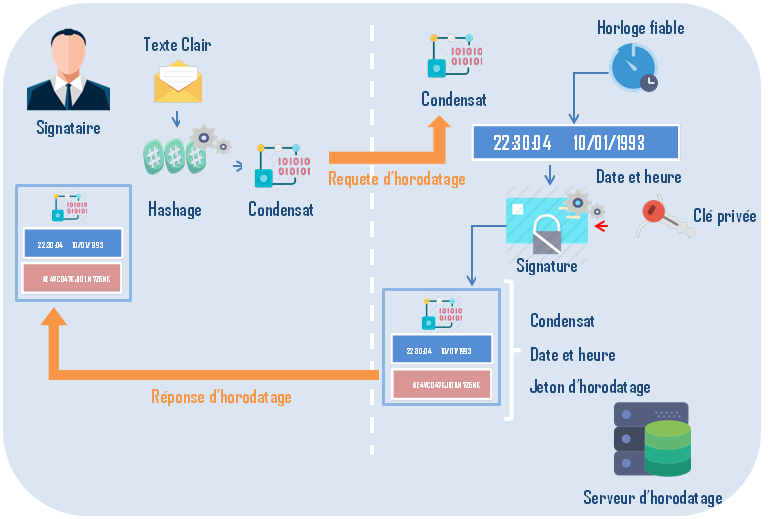
What is electronic time stamping ?
Many administrative procedures involve the date of dispatch of documents: submission of applications, replies to calls for tenders, various declarations, etc. Traditional mechanisms use the postmark.
The dematerialization of such procedures requires an electronic equivalent to this postmark.
The PKCS # 7 format that describes the signed data containers in the e-mail includes a field to indicate the date the message was signed.
However, the date and time of the signer's workstation are used in this field.
The sender can therefore cheat by indicating wrong dates.
Similarly, a malicious third party who has retrieved a private key associated with an expired certificate can artificially reduce the date of his machine within the validity period of the certificate and issue signed documents.
The electronic signature of a document is therefore inseparable from a mechanism that ensures that the document existed at a given date and time and has not been tampered with since. This is the time stamp.
It consists in transmitting to a trusted authority, called timestamp authority, a request including the condensate of the document to be timestamped.
The authority returns to the requester a time stamp, sthe
condensate, a date, and a time, all signed by the time stamping
authority.
